Using Integration Framework Services
LSOne Integration Framework services are available over the following protocols:
- net/tcp - default protocol used
- http - recomended only for development
- https - recomended for production
Before you can access the services provided by the Integration framework review the Integration Framework configuration file and make sure all settings are correct.
Using Integration Framework services over net/tcp
Required settings:
- Port set to a valid, free port in Integration Framework configuration file
- Machine name where Integration Framework runs
- The token for your client machine
Create a Service Factory the service factory will depend on the type of service you want to access
ChannelFactory<IIntegrationFrameworkRetailItemService> wcfRetailItemServiceFactory = new ChannelFactory<IIntegrationFrameworkRetailItemService>(binding, new EndpointAddress("net.tcp://" + address + ":" + port + "/" + IntegrationFrameworkItemServiceConstants.EndPointName))This will create a Service factory for the Integration framework retail item service where the address and port are parameters. After the service factory has been created it can then be used to return an instance of the service.
IIntegrationFrameworkRetailItemService wcfRetailItemService = wcfRetailItemServiceFactory.CreateChannel()The instance created will then give access to the full service contract this applies to all services created for the integration framework.
wcfRetailItemService.Get(itemId)
You need to make sure that the token value is sent with the request header. See Integration Framework Authentication for more details.
Using Integration Framework services over http
Required settings:
-
EnableServiceDiscovery set to true in Integration Framework configuration file
-
EnableHttpEndpoint set to true in Integration Framework configuration file
-
HttpPort set to true in Integration Framework configuration file
-
EnforceHttps set to false in Integration Framework configuration file
- Machine name where Integration Framework runs
- The token for your client machine
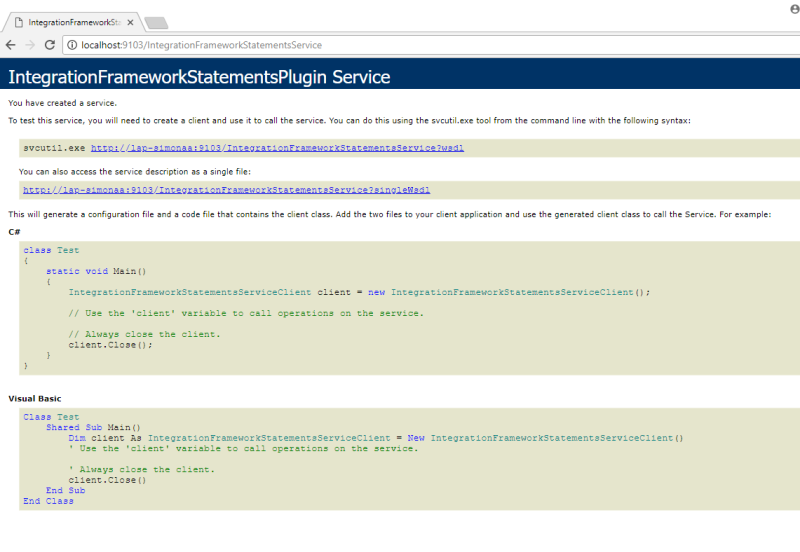
If configured correctly, Integration Framework endpoints and WSDLs can be viewed in the browser, by accessing:
-
http://MachineName:HttpPort/IntegrationFrameworkCustomerService
- http://MachineName:HttpPort/IntegrationFrameworkRetailDepartmentService
- http://MachineName:HttpPort/IntegrationFrameworkRetailDivisionService
- http://MachineName:HttpPort/IntegrationFrameworkRetailGroupService
- http://MachineName:HttpPort/IntegrationFrameworkRetailItemService
- http://MachineName:HttpPort/IntegrationFrameworkStatementsService
- http://MachineName:HttpPort/IntegrationFrameworkTransactionService
- http://MachineName:HttpPort/IntegrationFrameworkVendorService
Add the needed Integration Framework endpoints to your project as Service References. Visual Studio will generate the correct bindings for the service(s).
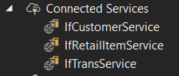
In the code:
IfCustomerService.IIntegrationFrameworkCustomerService wcfCustomerService = new IfCustomerService.IntegrationFrameworkCustomerServiceClient(endpointConfigurationName, httpUrl)wcfCustomerService.Get(customer.ID)
You need to make sure that the token value is sent with the request header. See Integration Framework Authentication for more details.
Using Integration Framework services over https
Required settings:
-
EnableServiceDiscovery set to true in Integration Framework configuration file
-
EnableHttpEndpoint set to true in Integration Framework configuration file
-
HttpPort set to true in Integration Framework configuration file
-
EnforceHttps set to true in Integration Framework configuration file
-
SslCertificateThumbnail set to a valid SSL certificate thumbnail in Integration Framework configuration file
-
SslStoreLocation set to the SSL certificate location in Integration Framework configuration file
-
SslStoreName set to the SSL certificate store name in Integration Framework configuration file
- Machine name or DNS name where Integration Framework runs
- The token for your client machine

The SSL certificate must be generated for the machine where Integration Framework will run such that the certificate subject or additional DNS entries match the machine name.
In PRODUCTION environments the SSL certificate must be obtained from a well-known CA like Verisign
Generate and install a self-signed certificate for development
For convenience there is a Powershell script in the DevPack/IFSamples/SelfSignedDevCert that generates a CA self-signed certificate and a self-signed certificate for the current machine, signed by the generated CA.
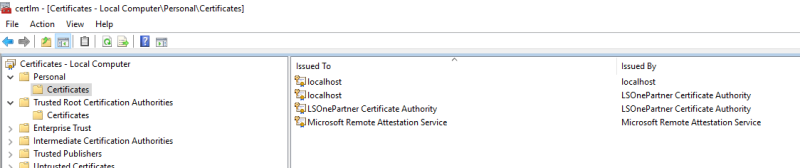
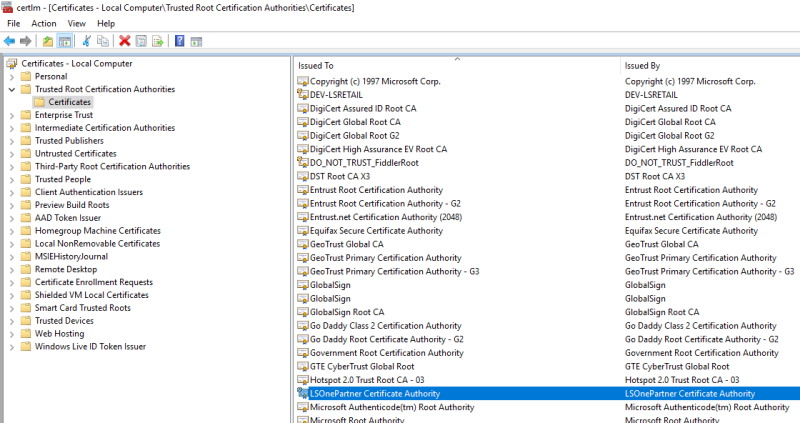
After running the script with administrative rights, open the Certificate Manager and verify that in LocalMachine / My there is a certificate having LSOnePartnerDev as friendly name and in LocalMachine/Trusted there is a certificate called LSOnePartner Certificate Authority.
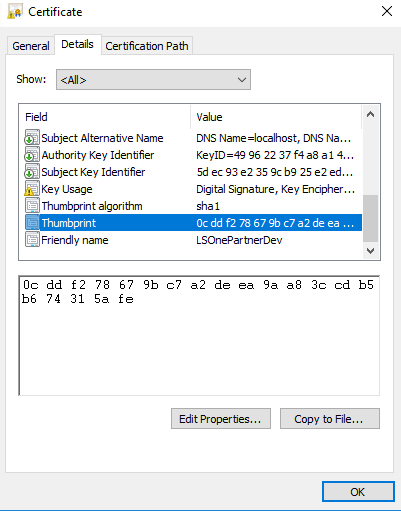
Duble click the LSOnePartnerDev certificate … Details …Thumbnail - copy the thumbnail string and remove any space between the letters and digits (you could paste it in Notepad++).
The last step is to bind the certificate to the Integration Framework http port based on the certificate thumbnail. Open a Command Prompt with administrative rights and enter
netsh http add sslcert ipport=0.0.0.0:9103 certhash=2995e4b0e8ac9052b06f9aca8be994c8e286016c appid={73a11591-6eb8-4b99-baa3-2bd1169ec10e}where
- 0.0.0.0 means all network interfaces,
- 9103 is the Integration Framework http port,
2995e4b0e8ac9052b06f9aca8be994c8e286016c is the certificate thumbnail
{73a11591-6eb8-4b99-baa3-2bd1169ec10e} is the SiteService application GUID
If the Integration Framework http port or the certificate are changed, the previous binding must be removed with:
netsh http delete sslcert ipport=0.0.0.0:9103
After installing and configuring the SSL certificate, the Integration Framework services are available over https and can be checked in any browser.

Latest versions of Chrome browser do not allow accessing sites using self-signed SSL certificate. To bypass this security border, open a new tab in Chrome and in the Address tab input: chrome://flags/#allow-insecure-localhost
Activate "Allow invalid certificates for resources loaded from localhost"